Since 2019, a host of dark web marketplaces have been struggling to stay afloat amid the barrage of distributed denial-of-service (DDoS) attacks that have targeted the users and operators of darknet platforms.
In theory, a DDoS attack denotes the malicious cyber technique involving disruption of the normal traffic of a network by threat actors seeking to overwhelm their target with a flood of internet traffic.
In simple terms, a DDoS attack can be metaphorized as a traffic snarl-up clogging up a road thus hampering the smooth flow of regular traffic. These attacks have been felt by a number of dark web platforms such as Dream Market and Nightmare market that top the list of lost popular darknet marketplaces today.
Empire Market’s Woes and Exit Scam Suspicions
An August 25, 2020 message posted on the Dread forum intimated that Empire Market is currently struggling to recover from an ongoing DDoS attack by unknown actors.
The statement sought to provide an explanation to user grievances that the platform had become slow to access, and that its Monero functionality had been impaired.
The post on Dread, which written by user /u/Melbourne on behalf of Empire Market, claimed that the site is currently “working tirelessly” to overcome the attack.
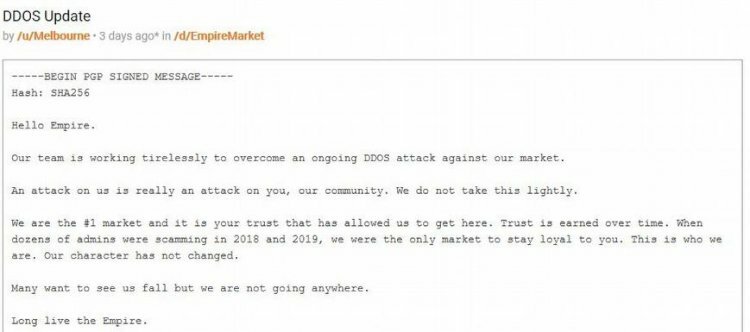
A statement on Dread by Empire Market concerning the ongoing DDoS attack.
According to the official statement, the site admins have taken the DDoS attack very seriously considering the scale of damage it’s bound to cause to Empire vendors and customers. On an interesting note, the statement reassured Empire users that the market “is not going anywhere” despite the long list of exit scams that have since happened in the dark web space – an aspect that highlights the connection between DDoS attacks and exit scams.
The above premise is evidenced by the spate of Reddit user comments who believe that Empire Market could be planning to scam its users through a well-planned exit strategy, meaning that the crypto managed by the marketplace will vanish as operators close shop.
In addition, a Twitter user has claimed that Empire Market operators have already transferred tens of millions of funds in Bitcoin to unknown wallets during the platform’s downtime.
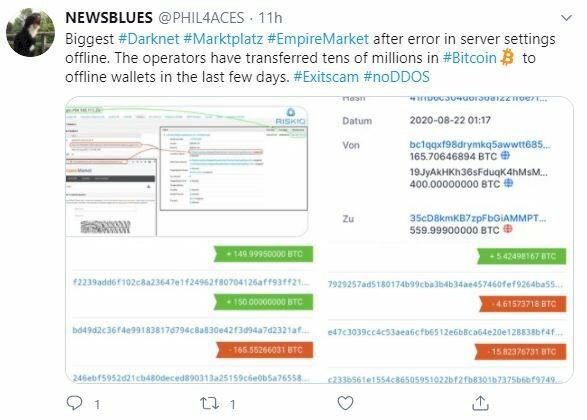
A tweet accusing Empire Market of moving user funds (Source: Twitter)
However, these accusations have been challenged by other users who have come out to dispel the thesis, arguing that this is not the first time that Empire Market has suffered a regular DDoS attack and recovered from it.
The Lethality of DDoS Attacks
In the past, DDoS attacks have been known to cripple entire darknet marketplaces, with Dream Market having considered a shutdown after sustaining a barrage of the attacks in a period of more than seven weeks.
According to the platform’s moderator, an unknown threat actor had launched the series of attacks in demand for ransom payments amounting to $400,000 in order to cease the DDoS assault.
It turns out that Dream Market’s operators were not willing to yield into the extortionist’s demands who is reported to have taken advantage of a vulnerability in Tor’s network to undermine the darknet platform.
Interestingly, just after Dream Market had made the announcement to wrap up operations owing to their cyber predicament, the DDoS attacks ceased and shifted focus to other websites – with Empire Market being the prime target.
Point to note, a wide range of other DDoS attacks have been orchestrated to target Nightmare Market and Wall Street Market, which was accused of exit-scamming its users.
In terms of possible DDoS attackers, it is still unclear whether the initial threat actors have been responsible for all known DDoS onslaughts, including the latest Empire Market attack.
In addition, no one knows whether competing platforms, or even underground law enforcement agents, have been responsible for the DDoS attacks created to cripple operations within popular darknet markets.
jabber: onionlover@xmpp.jp
PGP